(Global) IT Security-Strategy RoadMap
In today’s world-wide economy, every Company, in every Industry, in every Country, must take steps to protect themselves. It’s a common maxim that states – “It’s not IF you will get Hacked…. But WHEN...”
Several catastrophic data-breaches have happened lately that has shaken even the U.S. Citizens and the American economy – specifically, the EQUIFAX Data-Breach, where where both the CIO and the CEO were fired for negligence – and is expected to cost them almost $1 Billion to settle (currently at $750MM).
CLOUD-Computing Security (AWS / Azure / GCP / IBM)
Many companies are transitioning to ‘Cloud-Computing’, but most don’t realize that almost All Security standards are the Responsibility of the Customer. We can provide BOTH the Technical (Hardening) Standards and Procedural (document) Standards, that Cloud-Vendors like Amazon and Microsoft require in order to ensure the security of your Data and systems. We can also help to design and implement Role-Based Access-Control (RBAC) and Identity-and-Access-Management (IDM) to greatly reduce the effort and man-hours required to administer and manage the End-Users in your Cloud environment.
Whether it's Amazon's AWS Cloud, Microsoft Azure, IBM's Cloud, or Google Cloud - we have the technical professionals with the hands-on experience to help guide you in creating a Secure Infrastructure (Public, Private or Hybrid).
(Enterprise-wide) Risk-Assessment and (controls) Gap-Analysis
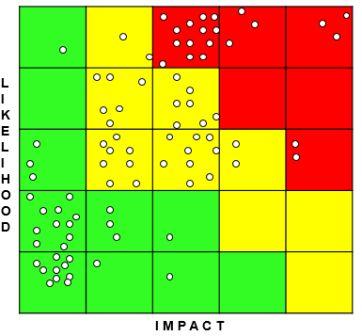
Risk-Assessment / Management is the defined, repeatable process, performed bi-yearly, of proactively Identifying, Analyzing, and Evaluating Risk at the company-level, and Developing Risk-Treatment and/or Mitigation plans and Executing those plans to eliminate, avoid or transfer that Risk out of the organization, with the intent of reducing the Residual Risk to an acceptable level. An effective Risk-Management Plan will identify the critical infrastructure in the company and evaluate the key controls relevant to those systems / processes and verify that – the Control exists, whether the Control is Functioning (well), etc. The result of the evaluation will be a Gap Analysis and an Action or Remediation Plan to address the GAP(s) based n their Risk and Cost (time, dollar, redesign, etc.). The security-related portions of the Remediation Plan become Mission-Critical Projects / Programs on the Security-RoadMap. When Management determines what the company’s Risk-Tolerance is for Financial Loss, Reputational Loss, Loss of Business, etc. then the analysis of the results becomes a simpler process that can be initiated by Line-Management if needed. Because the results are based on the risk to the company, even Audit and Compliance will support the efforts and decisions.
Penetration (Pen) Testing and Network Security
Commonly called ‘Ethical Hacking', 'White-Hat' testing or Pen-Test’, this is an authorized, Simulated attack on the company’s computer system (and Network), performed to evaluate the security of the system as a whole. The test is performed to identify weaknesses (referred to as Vulnerabilities), and the potential for unauthorized parties to gain access to the system’s features and data and is usually part of an Audit or Annual Risk Assessment. Common Tools include – nMap, Nessus, Burp-suite, Metasploit, THC-Hydra, etc. The value of this activity is the highest among comparable methods. The test will identify the weakest points in the network as well as identify many common compound-vulnerabilities in your technology stack.
Network Security is the process of segregating your Data into common types or uses and also physically "Segmenting" your network into relevant 'subnets'. Many Compliance Standards like PCI and HIPAA require companies to separate their Networks in logical segments, in order to provide for Defense-in-Depth and minimize the access or damage a Hacker can do if they manage to break into your Network. This also allows companies to Limit the Audit-Scope or Compliance-Scope of Review. This "Best-Practice" will surely pay for itself in the event of a Data-Breach. Plan ahead now.
Vendor / 3rd-Party Security Assessment
This process involves – researching and sourcing vendors, obtaining price quotes, capabilities, and quality of work, negotiating contracts, assigning jobs, processing payments, preventing Fraud and nowadays can include IT-as–a-Service, Data-Protection, and CLOUD-Security. Target and BOEING suffered multi-million dollar breaches via a Vendor. Common packages are Claritum, GateKeeper and SAP FieldGlass.
Key activities in this area include - evaluating a Vendor's Security Program, reviewing their latest Pen-Test Results, a Vendor-Scoring Program, Clauses in Legal / Vendor Contracts, Right-to-Audit stipulations, etc. Be sure to Hold your Vendors / Partners Accountable for Security - they could be Your Weakest Link.
. This will help companies avoid Data-Breaches as well as highly-publicized, potentially embarrassing events like The Panama Papers Data-Breach Incident.
Product / Service #3
Don't think of this product or service as your third favorite, think of it as the bronze medalist in an Olympic medals sweep of great products/services.
Product / Service #3
Don't think of this product or service as your third favorite, think of it as the bronze medalist in an Olympic medals sweep of great products/services.
Product / Service #3
Don't think of this product or service as your third favorite, think of it as the bronze medalist in an Olympic medals sweep of great products/services.
Since 1993
Your Main Message
Use this space to tell people what your company does and why and how it does it. What're you known for? Who likes you? What's your number one competitive advantage?
Include all the things that make your business unique and better than the competition. Do you have a patented 13-step process for taxidermy that results in the most lifelike stuffed owls? You gotta mention that.
Other good things to weave into this copy include: awards won, distinctions given, number of products sold, company philosophy (just keep it short), interesting company history bits, and anything that makes a reader think you'd be awesome to do business with.

(Enterprise-wide) Risk-Assessment and (controls) Gap-Analysis
Risk-Assessment / Management is the defined, repeatable process, performed bi-yearly, of proactively Identifying, Analyzing, and Evaluating Risk at the company-level, and Developing Risk-Treatment and/or Mitigation plans and Executing those plans to eliminate, avoid or transfer that Risk out of the organization, with the intent of reducing the Residual Risk to an acceptable level. An effective Risk-Management Plan will identify the critical infrastructure in the company and evaluate the key controls relevant to those systems / processes and verify that – the Control exists, whether the Control is Functioning (well), etc. The result of the evaluation will be a Gap Analysis and an Action or Remediation Plan to address the GAP(s) based n their Risk and Cost (time, dollar, redesign, etc.). The security-related portions of the Remediation Plan become Mission-Critical Projects / Programs on the Security-RoadMap. When Management determines what the company’s Risk-Tolerance is for Financial Loss, Reputational Loss, Loss of Business, etc. then the analysis of the results becomes a simpler process that can be initiated by Line-Management if needed. Because the results are based on the risk to the company, even Audit and Compliance will support the efforts and decisions.
Penetration (Pen) Testing and Network Security
Commonly called ‘Ethical Hacking', 'White-Hat' testing or Pen-Test’, this is an authorized, Simulated attack on the company’s computer system (and Network), performed to evaluate the security of the system as a whole. The test is performed to identify weaknesses (referred to as Vulnerabilities), and the potential for unauthorized parties to gain access to the system’s features and data and is usually part of an Audit or Annual Risk Assessment. Common Tools include – nMap, Nessus, Burp-suite, Metasploit, THC-Hydra, etc. The value of this activity is the highest among comparable methods. The test will identify the weakest points in the network as well as identify many common compound-vulnerabilities in your technology stack.
Network Security is the process of segregating your Data into common types or uses and also physically "Segmenting" your network into relevant 'subnets'. Many Compliance Standards like PCI and HIPAA require companies to separate their Networks in logical segments, in order to provide for Defense-in-Depth and minimize the access or damage a Hacker can do if they manage to break into your Network. This also allows companies to Limit the Audit-Scope or Compliance-Scope of Review. This "Best-Practice" will surely pay for itself in the event of a Data-Breach. Plan ahead now.
Vendor / 3rd-Party Security Assessment
This process involves – researching and sourcing vendors, obtaining price quotes, capabilities, and quality of work, negotiating contracts, assigning jobs, processing payments, preventing Fraud and nowadays can include IT-as–a-Service, Data-Protection, and CLOUD-Security. Target and BOEING suffered multi-million dollar breaches via a Vendor. Common packages are Claritum, GateKeeper and SAP FieldGlass.
Key activities in this area include - evaluating a Vendor's Security Program, reviewing their latest Pen-Test Results, a Vendor-Scoring Program, Clauses in Legal / Vendor Contracts, Right-to-Audit stipulations, etc. Be sure to Hold your Vendors / Partners Accountable for Security - they could be Your Weakest Link.
. This will help companies avoid Data-Breaches as well as highly-publicized, potentially embarrassing events like The Panama Papers Data-Breach Incident.
Product / Service #3
Don't think of this product or service as your third favorite, think of it as the bronze medalist in an Olympic medals sweep of great products/services.
Product / Service #3
Don't think of this product or service as your third favorite, think of it as the bronze medalist in an Olympic medals sweep of great products/services.
Product / Service #3
Don't think of this product or service as your third favorite, think of it as the bronze medalist in an Olympic medals sweep of great products/services.
Next Steps...
This is should be a prospective customer's number one call to action, e.g., requesting a quote or perusing your product catalog.